The Board-Ready CISO Report Deck [Template]
This editable template helps you communicate risk, impact, and priorities in language your board will understand—so you can gain buy-in and drive action.
Infrastructure Entitlements Management (CIEM)
Wiz analyzes cloud entitlements and auto-generates least privilege policies across your cloud, to help teams visualize, detect, prioritize, and remediate identity (IAM) risks.
Identities are the new perimeter in the cloud. Reduce attack surface with Wiz's effective permissions analysis to understand who can access what in the environment and detect identity-related risk and exposure.
Wiz detects identity risks such as excessive or admin permissions, high privileges, as well as identity misconfigurations such as no MFA enabled or inactive users.
Easily discover and remove identity attack paths that can lead to high-value assets such as admin identities or crown jewel data with cloud context on the Wiz Security Graph.
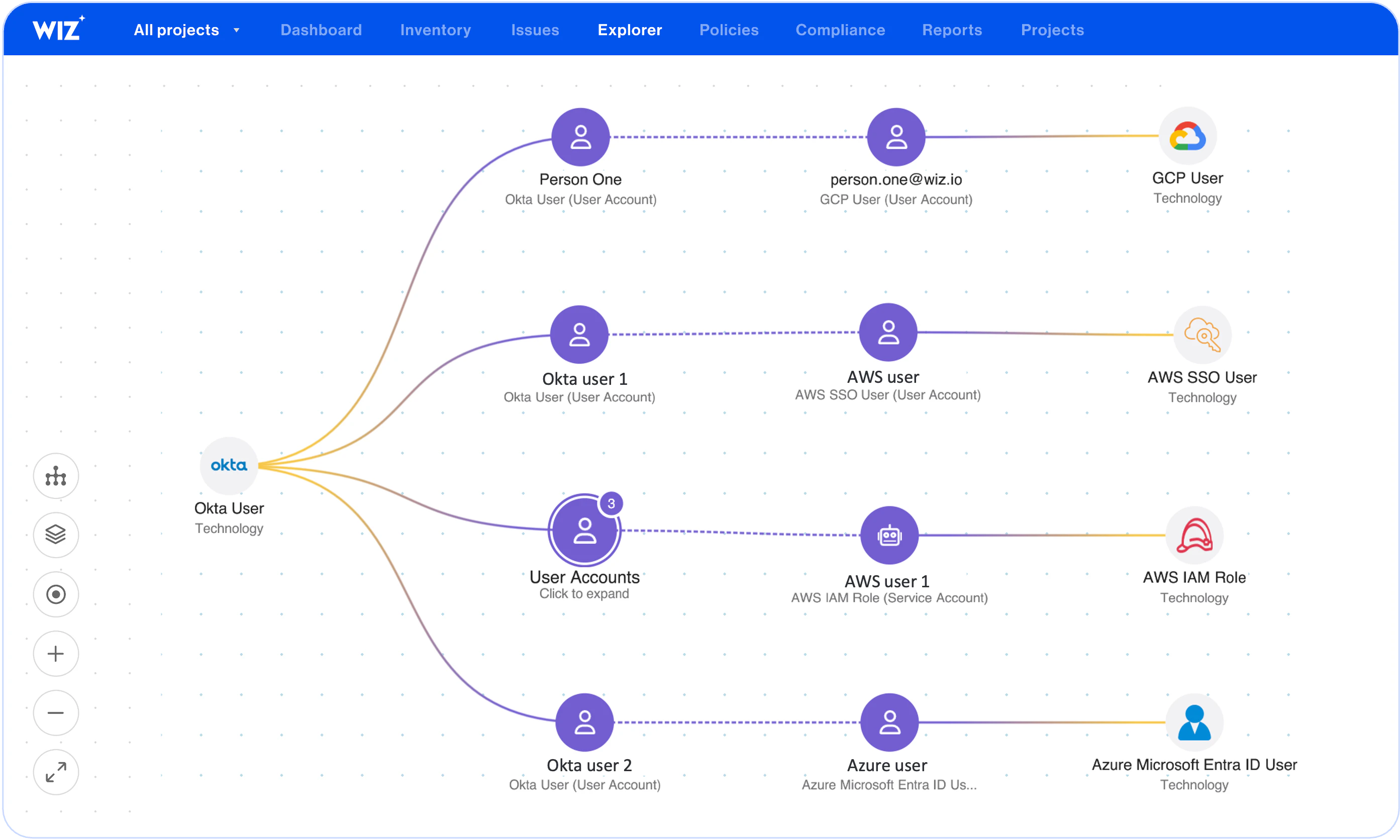
Effective permissions analysis for human and non-human identities to answer "who can access what in my environment" across IdP, SaaS, and cloud mapped on the Wiz Security Graph.








Wiz builds a map of effective access between all human, non-human identities, and resources, taking into account advanced cloud-native controls including boundaries, ACLs, SCPs, and RCPs. Understand cloud permissions of IdP users such as Okta, as well as SaaS permissions such as Snowflake users.
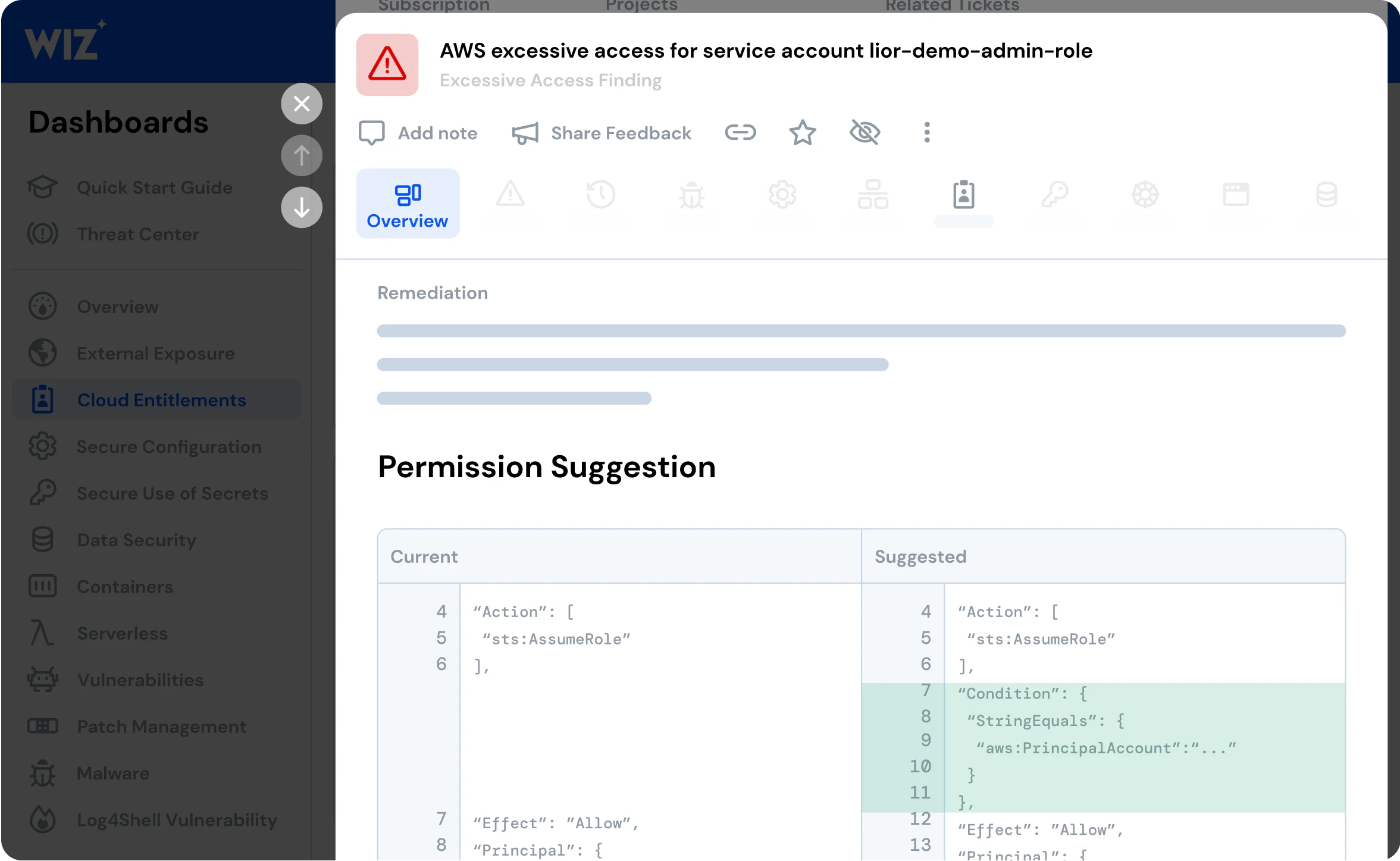
Wiz alerts you of IAM misconfigurations such as unused admin permissions, principles without MFA, or identities with excessive permissions and gives you guided remediation steps to reduce access and revoke unused permissions.
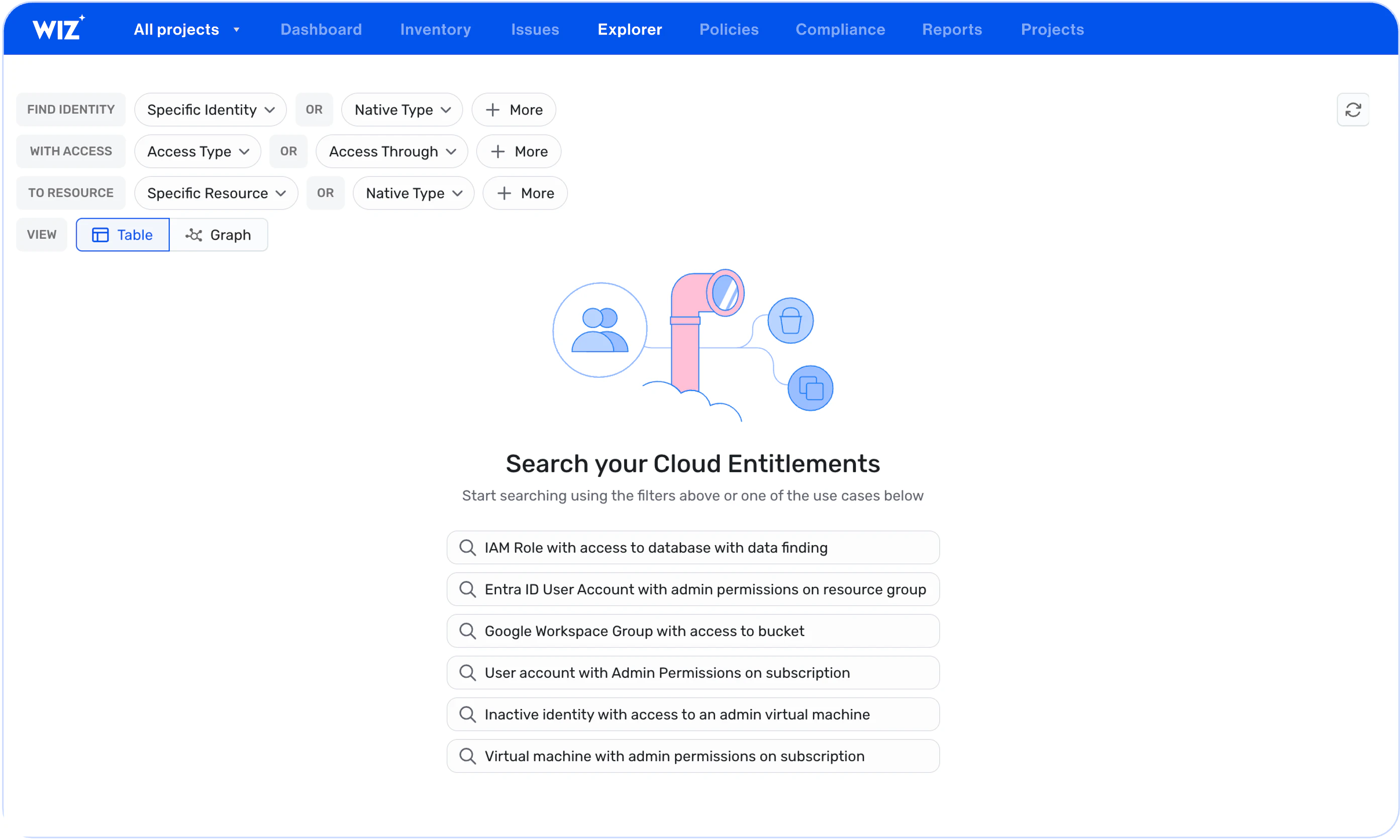
Easily query your cloud entitlements based on identity, access type and resource and simplify CIEM so anyone can understand cross-platform effective access.
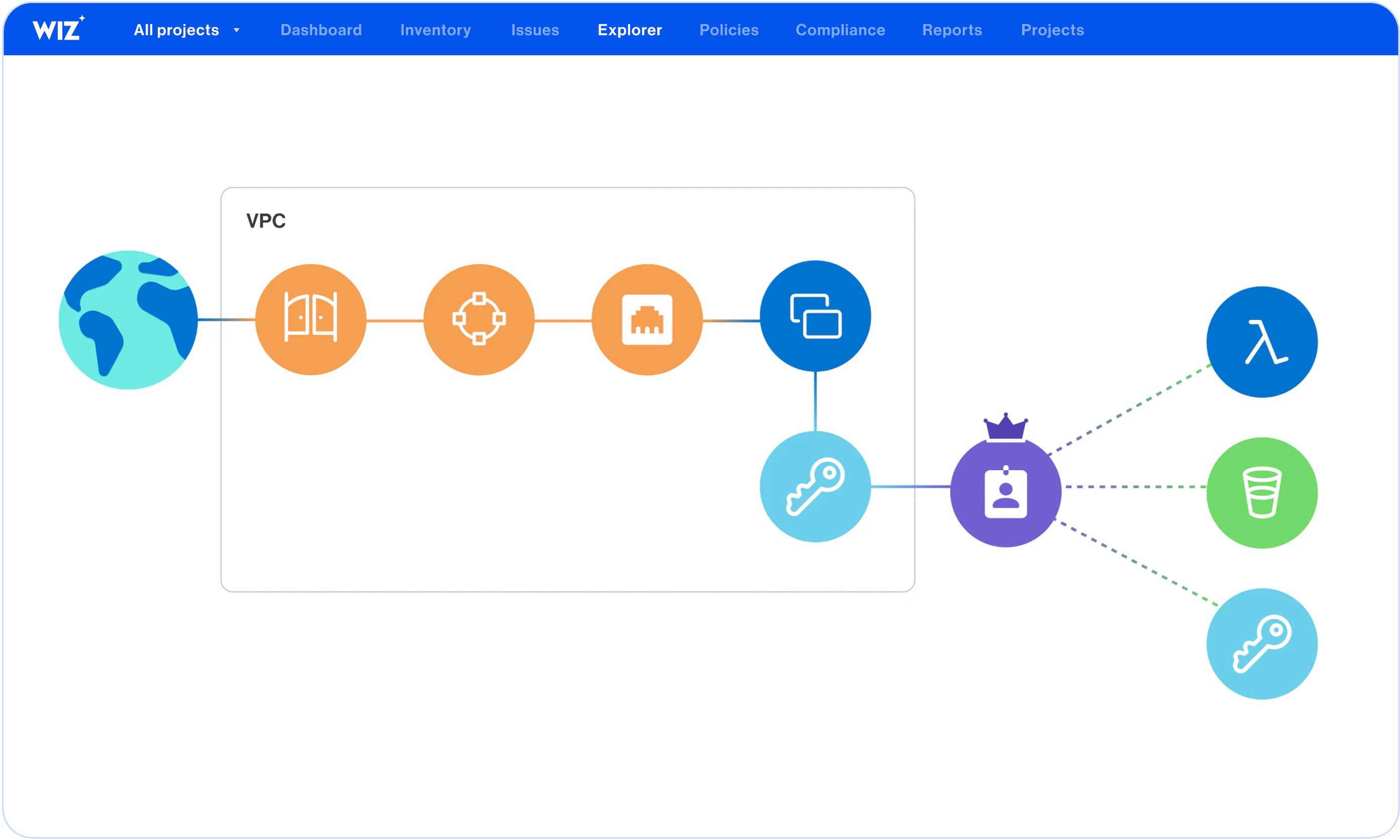
Wiz correlates cloud entitlements with data risks, vulnerabilities, misconfigurations and other risk factors to surface attack paths that represent your most critical risks to effectively improve your cloud security posture. For example, detect lateral movement paths to admin permissions or to sensitive data.
Wiz's agentless scanning detects exposed secrets and credentials that attackers might use in attempt to access sensitive assets or take over accounts and identifies complex lateral movement paths.
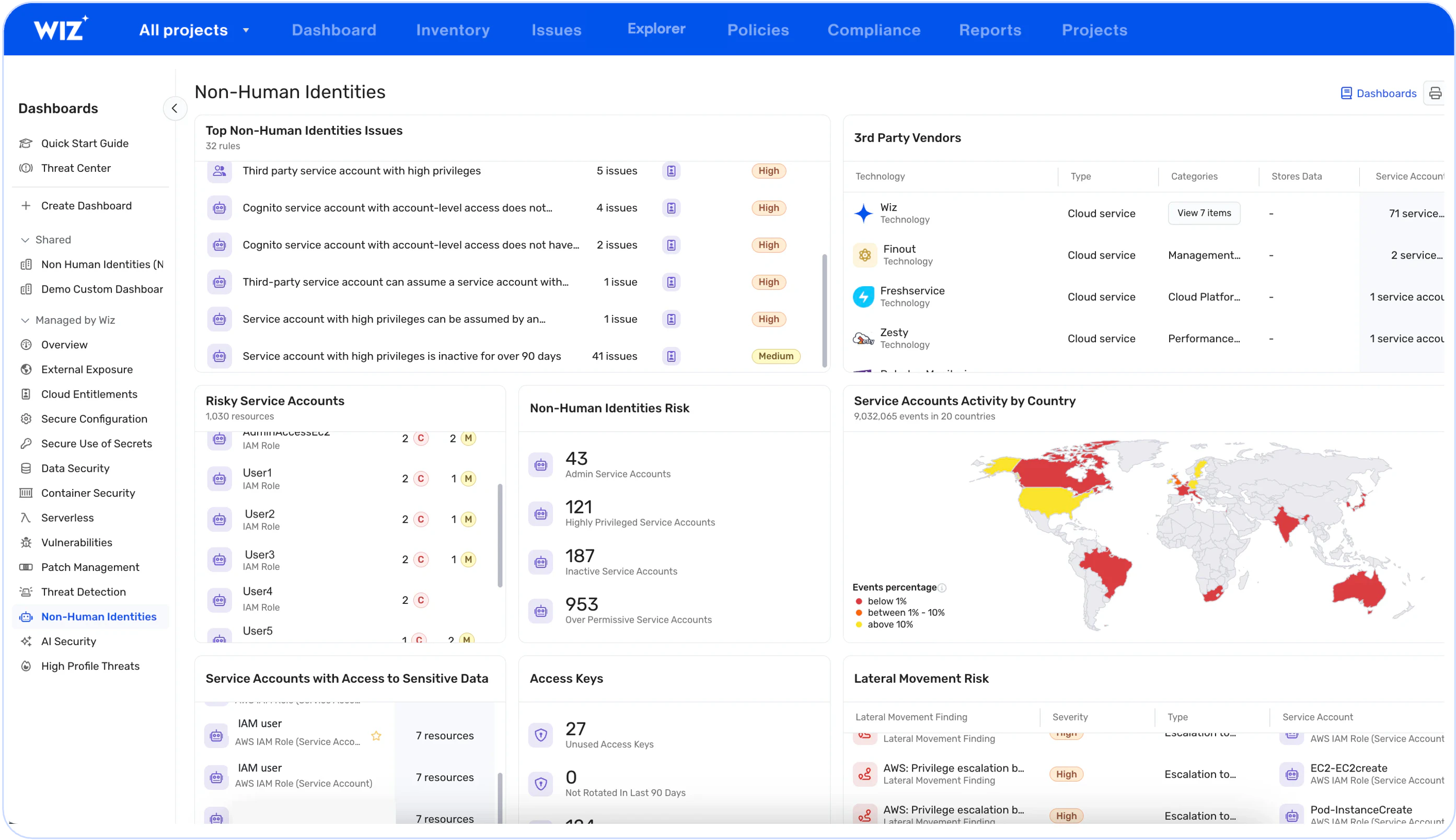
The Non-Human Identities Dashboard makes it easy to monitor non-human identities and their access in your environment. Detect risky service accounts, such as service accounts with admin or high privileges or third-parties that can access sensitive data.
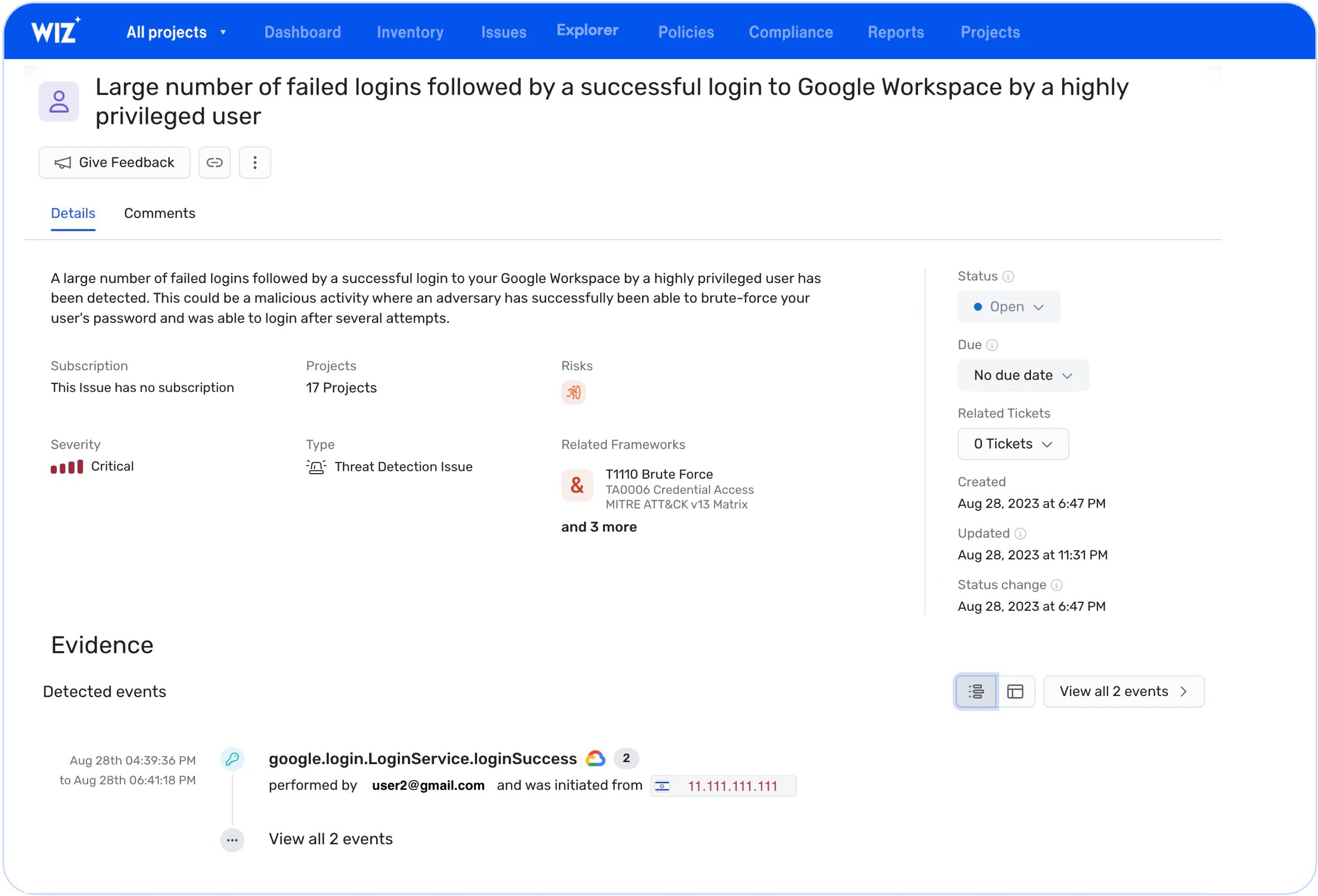
Wiz's threat detection rules allow you to quickly identify and respond to suspicious activity in your environment in real-time and understand blast radius on the Wiz Security Graph.
Get a personalized demo
"Best User Experience I have ever seen, provides full visibility to cloud workloads."
"Wiz provides a single pane of glass to see what is going on in our cloud environments."
"We know that if Wiz identifies something as critical, it actually is."