Data discovery and classification
Continuous agentless discovery of your sensitive data in code, IaaS, PaaS, DBaaS, and AI against built-in and custom classifiers. Easily answer "Where is my sensitive data located"?.
Data Security Posture Management (DSPM)
Continuously discover and classify sensitive data, detect data risks and attack paths with context, and automate compliance assessment against data regulatory frameworks.








Attack paths in the cloud are complex. Detecting data exposure is not enough. Wiz DSPM provides graph-based context allowing you to effectively remove attack paths to data.
Continuous agentless discovery of your sensitive data in code, IaaS, PaaS, DBaaS, and AI against built-in and custom classifiers. Easily answer "Where is my sensitive data located"?.
Automatically correlate your sensitive data with underlying cloud context, including public exposure, identities and entitlements, vulnerabilities, malware, and lateral movement to remove attack paths to sensitive data.
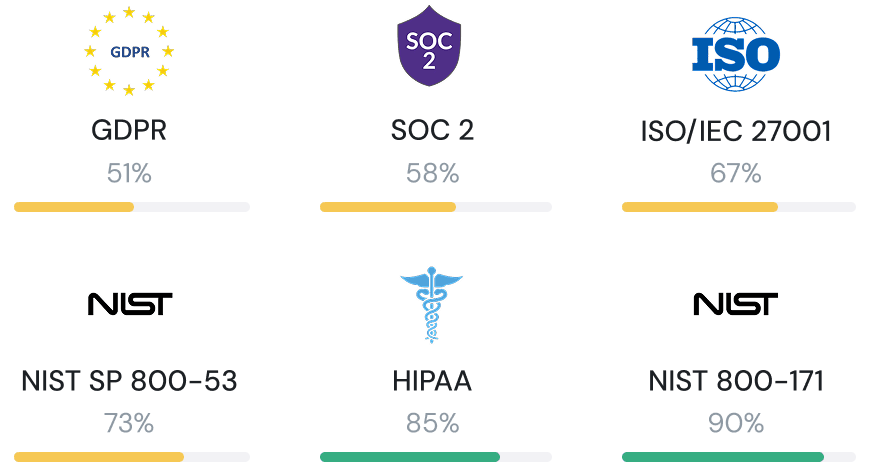
Continuously assess and report on your compliance posture against regulatory frameworks such as PCI DSS, HIPAA, HITRUST, and others. Ensure data sovereignty with a geographical view of data findings.
Easily answer "Who can access what data in my environment?" to ensure only authorized users to access sensitive data and remove excessive access to critical data.

Remove attack paths to critical data with context on the Wiz Security Graph
Identify who can access what data in the environment and detect IAM risks
Assess compliance posture against built-in data regulation frameworks
Detect sensitive training data in AI pipelines including OpenAI
Enhancing data findings with cloud and workload context delivers a data security solution that is specifically designed for detecting complex attack paths in the cloud.
Discover and classify sensitive data in your cloud with built-in classification rules including PII, PHI, PCI, and secrets or define custom classifiers, all without agents. Extend data scanning to code and CI/CD pipelines.
Detect attack paths to critical data using context on the Wiz Security Graph to easily answer which data is stored where, who can access what data, how data assets are configured and utilized , and how data moves across environments.
Continuously assess compliance against data security frameworks such as PCI DSS, GDPR, HITRUST, and others and identify geographical locations of sensitive data to ensure data sovereignty.
“ There was no technology in the industry that could provide the level of detail that Wiz does. ”
“ Because of Wiz, we’ve been able to democratize our approach to cybersecurity. Protecting our infrastructure is no longer concentrated in one team; the responsibility is distributed across the organization. ”
“ IT security governance has traditionally been somebody saying "You have to fix these vulnerabilities." Now, people can look up and say, "This is the attack path, and this is what I should do." ”
“ This new depth and breadth of visibility really made us pay attention. We were able to scan tenants and find new critical issues very quickly. ”
“ I'm a doctor, I take care of people, I was trained in preventative medicine. Wiz is like preventative medicine for us. ”
Get a personalized demo
"Best User Experience I have ever seen, provides full visibility to cloud workloads."
"Wiz provides a single pane of glass to see what is going on in our cloud environments."
"We know that if Wiz identifies something as critical, it actually is."