Wiz for FedRAMP
Wiz for Gov delivers FedRAMP-High authorized, agentless cloud security for federal agencies and contractors—helping accelerate compliance.
Government
Wiz for Government is a FedRAMP High authorized cloud security platform that accelerates cloud adoption and innovation with full visibility and continuous monitoring. Wiz automatically detects vulnerabilities, misconfigurations, exposed secrets, and over-privileged identities so teams can reduce risk fast.
Wiz is FedRAMP® High and GovRAMP authorized
Public sector organizations need a unified cloud security solution that helps:
Eliminate blind spots with agentless visibility across VMs, containers, serverless, Paas, and AI services. Wiz integrates into the software development lifecycle, unifying tools and processes from code to cloud to runtime.
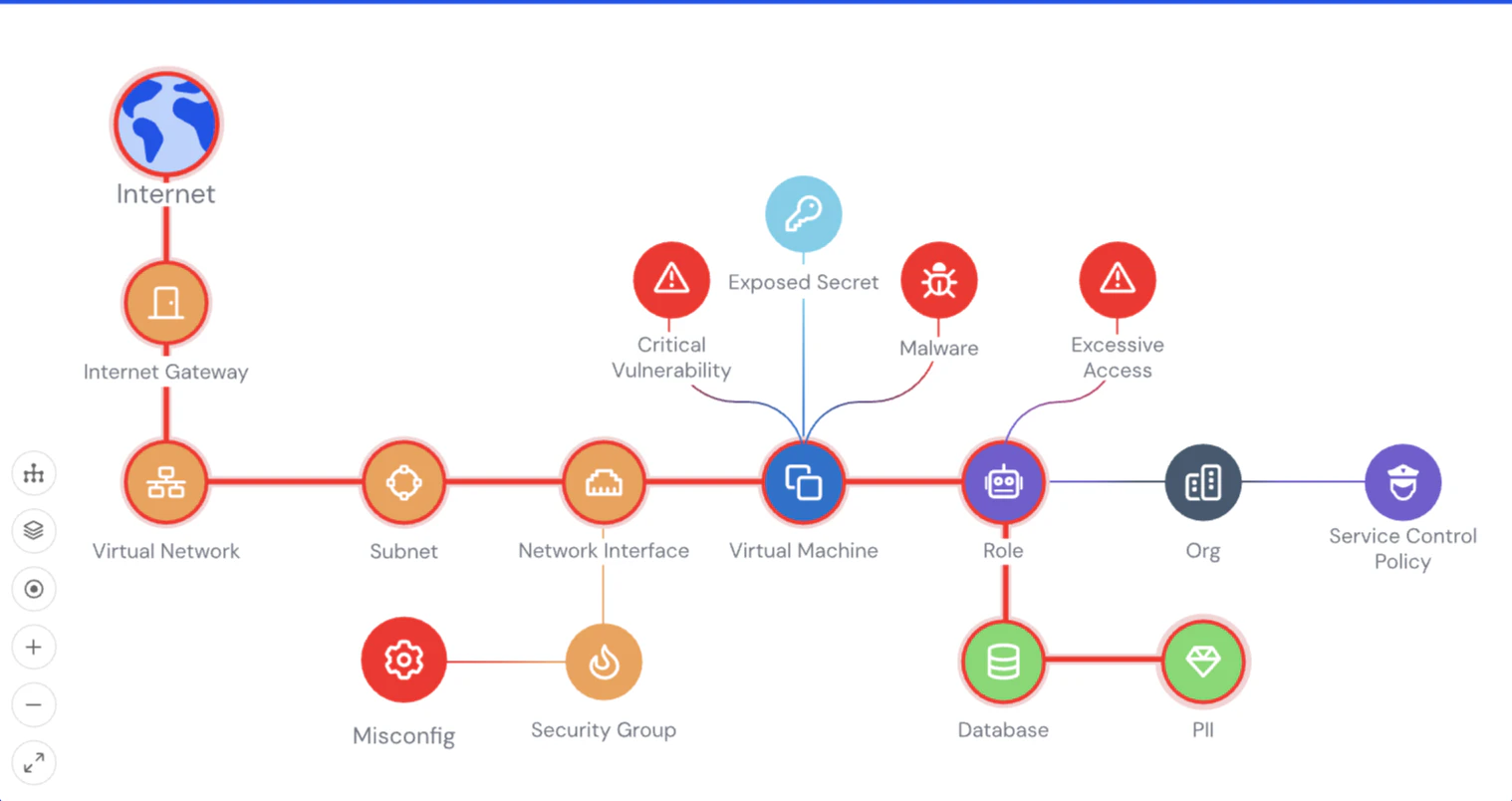
Continuously monitor risks across the software lifecycle. Automate discovery of vulnerabilities, misconfigurations, secrets, malware, excessive permissions, and insecure AI deployments. The Wiz Security Graph visualizes and prioritizes risks so teams can proactively remediate by impact.
Assess compliance posture against CIS Benchmarks, including Linux, Windows, and Red Hat STIG. Wiz automates discovery and reporting for inventory, vulnerabilities, SBOMs, and AI-BOMs, with built-in reports that make investigation easy.
Our security and privacy programs are audited on an annual basis against industry standards including SOC2 Type 2, ISO 27001, 27701, 27017, and 27018, and PCI.
Our product uses encryption technologies and services that meet FIPS 140-2 and FIPS 197 standards, and key management technologies that meet NIST SP 800-57 guidance. Learn more our FedRAMP solution here





Reference to any government customers herein does not constitute or imply endorsement, recommendation or favoring of any commercial company, products process or service by the United States Government or any of its agencies, departments or sub-entities.
The Wiz Cloud Native Application Protection Platform (CNAPP) empowers Development, Security, Compliance, and Operations teams to secure everything they build and run in the cloud.
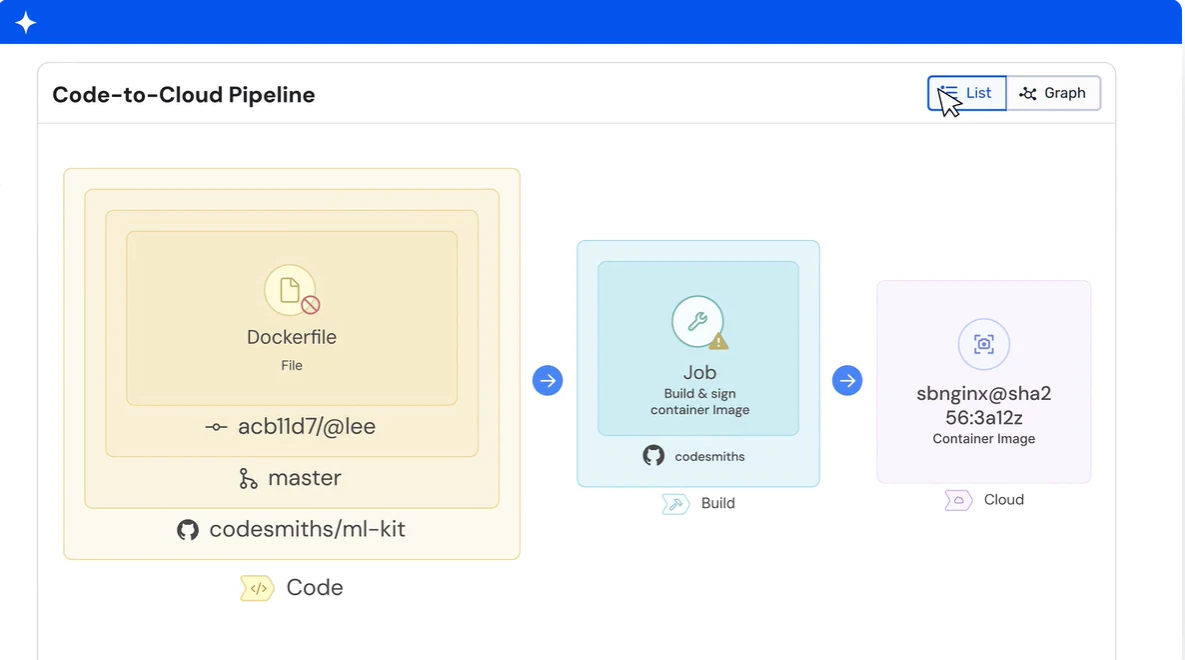
Help developers build securely by design during every stage of your SDLC. Wiz Code scans for vulnerabilities, sensitive data, misconfigurations, and secrets from code, pipeline, registries, and images. Applying scans and policies from IDE through the build pipeline allows you track developer configuration changes and integrity of the system by preventing unauthorized modifications.
Learn more: Wiz Code Product Page
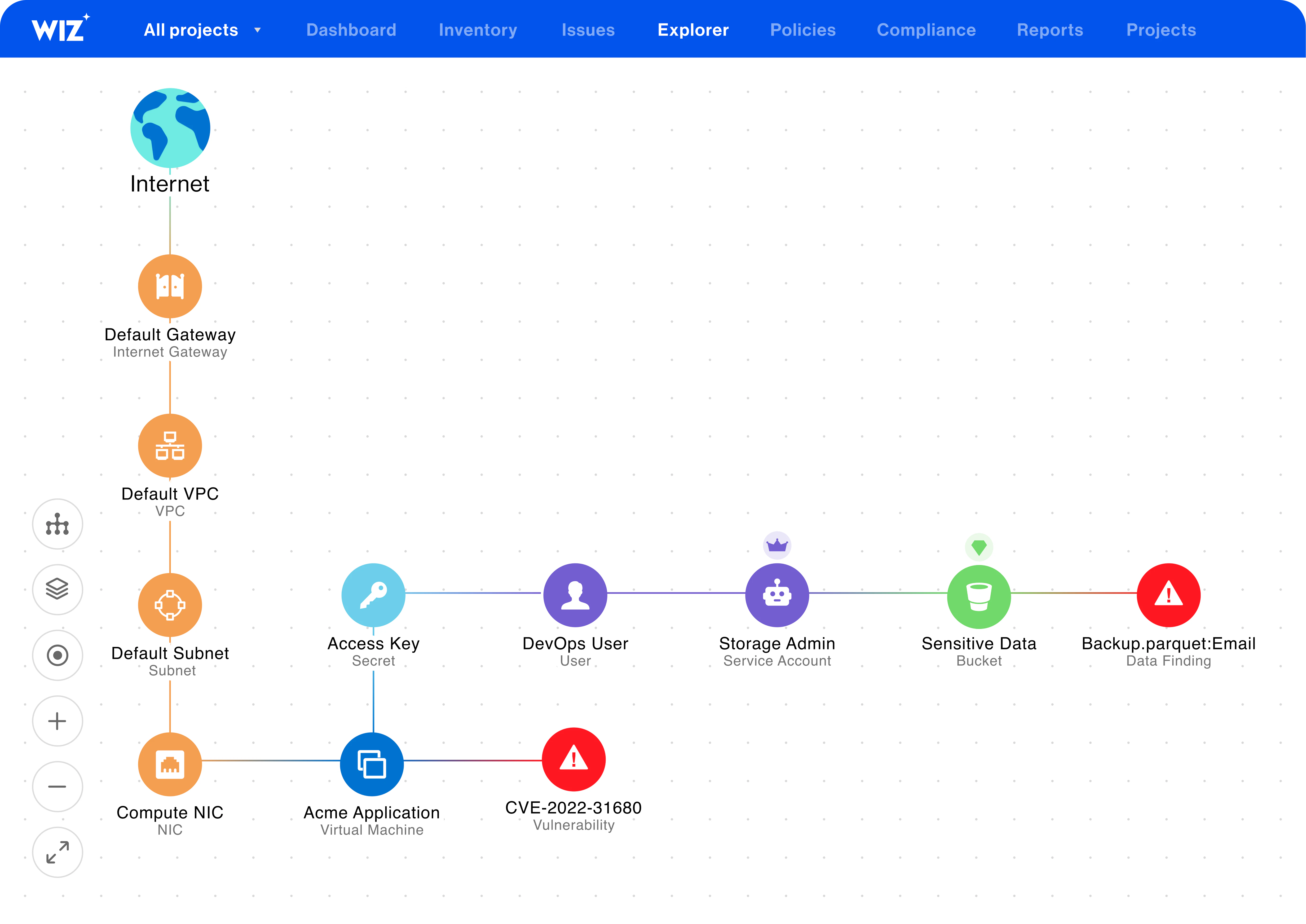
Wiz Cloud uses the Wiz Security Graph to deeply analyze hosted software to the infrastructure running it, pinpointing and prioritizing critical risks based on potential attack paths. This helps security teams continuously monitor baseline configurations, vulnerability and malware risks, and audit for privileged access.
Learn more: Wiz Cloud Product Page
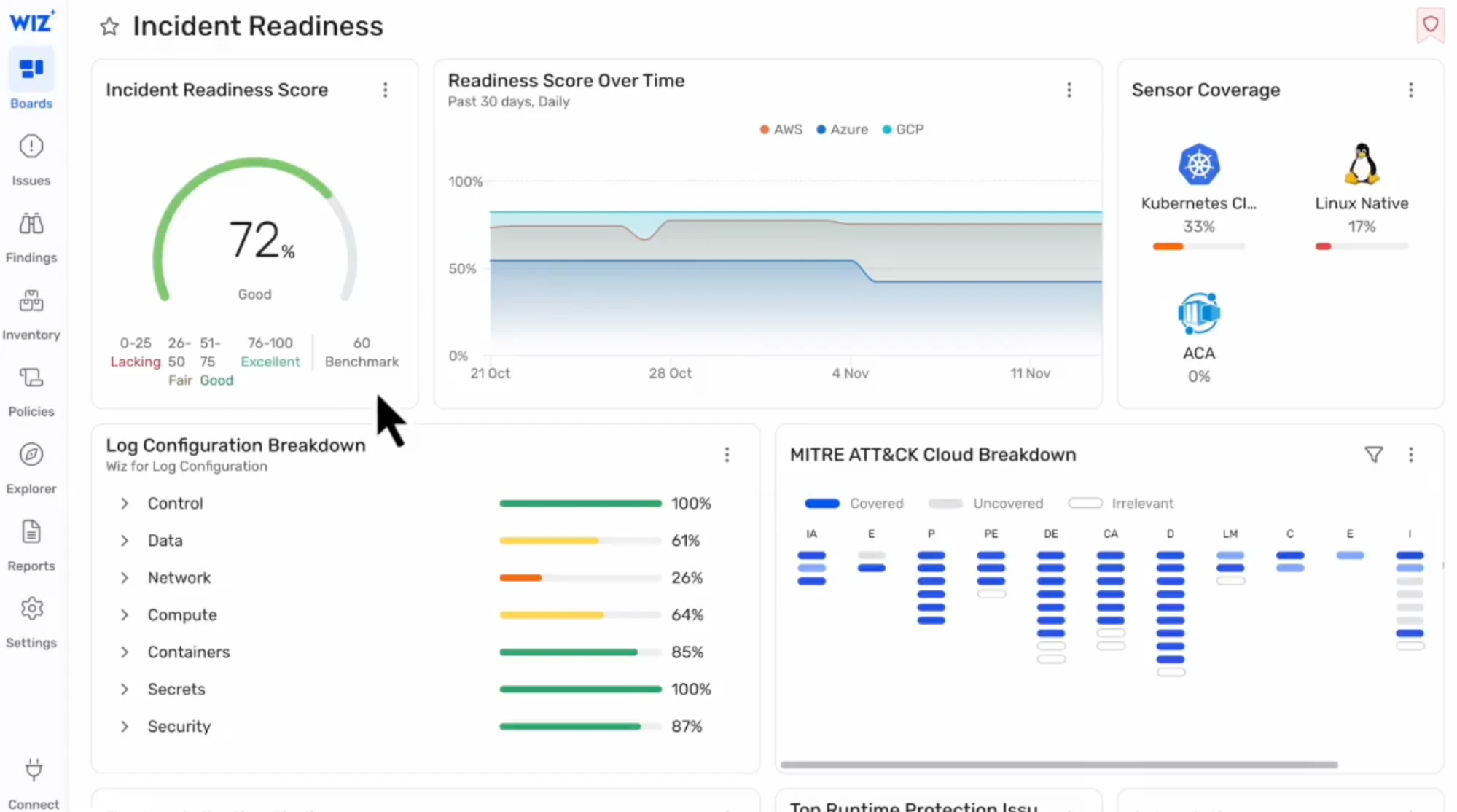
Provide teams with real-time cloud threat detection, and deep, process-level visibility and behavioral detection across VMs and containers to identify indicators of compromise (IOC). Accelerate response through unified runtime signals from the Wiz Sensor for host-based monitoring to enhance security impact analysis. Reduce alert noise and give SecOps teams code to cloud visibility for more effective remediation.
Learn more: Wiz Defend Product Page
Wiz Research delivers cutting-edge cloud threat intelligence, actively investigating and neutralizing emerging risks. Our experts enhance Wiz products with proprietary detections and contribute to public security initiatives for unparalleled protection. The team quickly creates dynamic rules to identify newly reported zero-day vulnerabilities (both discovered by Wiz and external parties) within Wiz customer environments to meet rapid reporting requirements by CISA, FedRAMP and others.
Learn more: Wiz Research Page
Accelerate your cloud migration with visibility and risk reduction. Build a secure foundation for your agency from the start.
Stay ahead of threats like the Log4j or MOVEit vulnerabilities and eliminate potential downtime with Wiz’s agentless vulnerability scanning. Identify exposures to emerging vulnerabilities in the Threat Research Center.
Remove operational silos between cybersecurity, compliance, and developers so you can scale security across your agency. Enable development teams to proactively fix and prevent issues across their development lifecycle with context and prioritization.
Wiz helps you ensure Zero Trust in your environment by providing visibility & assessing risk across the five pillars of the Zero Trust Maturity Model.
Gain visibility into the identities and permissions in your environment. Understand effective permissions and identify identity-related risk and exposure including excessive permissions and lateral movement paths.
Case study
Wiz equips U.S. Navy customer with comprehensive visibility, preparing it to revolutionize its approach to cloud security.
Read full storyGet a personalized demo
"Best User Experience I have ever seen, provides full visibility to cloud workloads."
"Wiz provides a single pane of glass to see what is going on in our cloud environments."
"We know that if Wiz identifies something as critical, it actually is."