Main takeaways from this article:
SecDevOps integrates security from the start of the software development lifecycle, ensuring vulnerabilities are addressed proactively.
DevSecOps and SecDevOps differ primarily in their approach and emphasis on embedding security into the DevOps process.
SecDevOps integrates security early in the software development process lifecycle, ensuring vulnerabilities are addressed proactively.
Key components of SecDevOps architecture include shift-left security, automation, collaboration, and continuous monitoring.
Best practices for SecDevOps involve automating security, engaging developers in security training, and managing dependencies securely.
What is SecDevOps?
SecDevOps is an evolution of the DevOps approach, with a strong emphasis on integrating security earlier in the software development life cycle, often referred to as "shifting security left."
In traditional DevOps, the development and operations teams collaborate to streamline workflows, enhance deployment efficiency, and deliver services more quickly to customers. SecDevOps builds on this by embedding security into every phase of the development and operations process, ensuring that potential vulnerabilities are identified and addressed as early as possible.
While security has always been a part of DevOps, the emergence of terms like SecDevOps and DevSecOps highlights the growing importance of proactively incorporating security into every step of the software delivery process rather than treating it as an afterthought or final checkpoint.
The State of Code Security Report [2025]
Security must be a core part of DevOps, but CI/CD security remains a weak link. The State of Code Security Report 2025 found that 35% of enterprises use self-hosted runners with poor security practices, making them a prime target for attacks.
Download reportSecDevOps vs. DevSecOps
While both SecDevOps and DevSecOps aim to enhance security, they differ in their approach and focus:
Security integration point: DevSecOps sees security as a shared responsibility that is integrated throughout the entire lifecycle, starting from initial design to deployment and beyond. SecDevOps emphasizes security but also prioritizes integrating it particularly early in the development process, often referred to as "shifting security left."
Primary focus: In DevSecOps, the goal is to ensure security without disrupting the agility and speed of DevOps. SecDevOps, on the other hand, focuses on incorporating security from the very first stages and maintaining it continuously.
Implementation strategy: DevSecOps employs a more balanced approach, treating security as one of three core components (development, security, operations). SecDevOps is more security-centric, embedding security measures into every phase, from planning to deployment.
Role of automation: Both methodologies leverage automation, but SecDevOps places a stronger emphasis on automated security testing and continuous monitoring right from the start.
DevOps Security Best Practices [Cheat Sheet]
In this 12 page cheat sheet we'll cover best practices in the following areas of DevOps: secure coding practices, infrastructure security, monitoring and response.
Download Cheat SheetWhy is SecDevOps important?
Implementing SecDevOps has many benefits and is crucial to building resilient software systems. Let's explore some of its benefits below.
Early detection of security concerns
One of SecDevOps's primary goals is the early detection of security concerns. By integrating security practices and tools from the very beginning of the software development lifecycle, potential vulnerabilities are identified and mitigated using:
Static application security testing (SAST): This technique examines the source code or binary code of applications for vulnerabilities without executing the code. It helps catch issues during the coding phase, allowing developers to fix them before they become more complicated.
Dynamic application security testing (DAST): Unlike SAST, DAST involves executing the application and simulating attacks to identify vulnerabilities. This helps uncover security flaws that may not be detectable through static analysis.
Interactive application security testing (IAST): Combining elements of both SAST and DAST, IAST provides real-time insights by analyzing an application from the inside while it runs. This hybrid approach helps to identify a broader range of vulnerabilities.
Faster time-to-market
SecDevOps integrates security early in the development process, allowing teams to detect and address potential vulnerabilities and bottlenecks from the outset. This, in turn, leads to:
Reduced rework: Early identification of security issues means fewer bugs are discovered later, reducing the need for rework and optimizing the development timeline.
Minimized compliance delays: Continuous security and compliance checks ensure that the software meets necessary regulatory standards early, avoiding last-minute compliance hurdles.
Proactive threat mitigation: Early security integration allows teams to proactively address potential threats, leading to a more secure codebase that requires fewer patches and updates post-deployment.
Enhanced collaboration
SecDevOps promotes better collaboration between security, development, and operations teams, creating a unified approach to secure, efficient, and high-performing software. Here's how:
Security is everyone's responsibility: By integrating security practices early, all team members—from developers to operations staff—understand their role in maintaining security, leading to a shared sense of ownership.
Improved communication: Regular interaction and feedback loops between teams ensure that security concerns are promptly addressed and solutions are collaboratively devised.
Unified workflows: Security tools and practices are integrated into the same workflows used by development and operations, making security a smooth part of the process rather than an afterthought.
Reduced risk of breaches
SecDevOps reduces the risk of breaches by embedding security practices throughout the entire development lifecycle through:
Early detection of vulnerabilities: By shifting left with security, potential threats and vulnerabilities are identified during the initial phases, enabling teams to address them before they become big issues.
Continuous security validation: Automated security tests in CI/CD pipelines ensure that each code change is scrutinized for security weaknesses, creating a consistent and secure development process.
Real-time monitoring: Continuous monitoring and feedback loops provide real-time insights into the application's security posture, allowing for immediate responses to potential threats.
Compliance and governance
By embedding security practices throughout the software development lifecycle, organizations can ensure compliance with relevant regulations and government frameworks, and SecDevOps helps with just that. Here's how:
Policy enforcement: Automated security checks enable consistent application of policies and standards, ensuring all code and configurations comply with regulatory requirements.
Governance alignment: Integrating security into CI/CD pipelines ensures that governance frameworks are adhered to from the initial stages of development to deployment.
Documentation and reporting: Automated tools and processes provide detailed documentation and reporting, which are essential for compliance verification and ongoing governance.
Improved customer trust
Consistently delivering secure applications is paramount in building customer confidence and trust in your brand. Implementing SecDevOps principles ensures this is taken care of. Here's how:
Data protection: When customers know that their personal and sensitive data is safe, they are more likely to trust and continue to use your platform.
Reduced churn rate: When security breaches are minimized, customer dissatisfaction decreases, resulting in lower churn rates.
Competitive advantage: Offering powerful security can set you apart from competitors, attracting customers who prioritize data protection and privacy.
Cost efficiency
Detecting security issues early in the software development lifecycle is crucial for cost efficiency. SecDevOps helps with just that. Here's how:
Reduced remediation costs: Fixing vulnerabilities during the development phase is often far less costly than addressing them post-deployment, where they may require extensive code rewrites or even system overhauls.
Lower operational disruption: Early detection ensures that security issues are resolved before they disrupt critical operations, avoiding downtime and maintaining service continuity.
Fewer resource allocations: By catching issues early, development teams can focus their resources more efficiently without needing emergency response efforts that can drain budgets and manpower.
Integrating SecDevOps into the software development lifecycle
SecDevOps entails the security, development, and operations teams working together to improve performance while enforcing a strong security posture. To effectively achieve this, you need to integrate security as early as the concept stage and maintain it throughout the entire software development lifecycle (SDLC).
Key elements of SecDevOps architecture:
Shift-left security: Security is embedded into early stages like planning and coding.
Automation: Security testing is automated in CI/CD pipelines to maintain speed and consistency.
Collaboration: Security is integrated into the same workflows that development and operations teams use, fostering collaboration.
Continuous monitoring and feedback: Monitoring tools ensure constant vigilance, allowing for real-time detection and feedback loops that help maintain secure operations.
In the image above, you can see an example of how security is embedded throughout the DevOps pipeline. From the planning stage, where threat modeling and risk assessments are conducted, to the deployment phase, where security configurations are reviewed, each step incorporates specific security practices designed to catch vulnerabilities early. Security automation and real-time monitoring are essential components that enable teams to rapidly detect and remediate issues before they can escalate.
The concept of continuous security is not only a technological shift but also a change in mindset—from viewing security as a set of security tools or products to seeing it as an ongoing process.
Top SecDevOps challenges
Like all positive developments, challenges to adoption exist. Here’s a few notable hurdles:
Skills shortage
One of the biggest hurdles to achieving SecDevOps is talent scarcity, as it requires developers and operations engineers who are highly experienced in security best practices. Because of this skills shortage, the existing pool is expensive and harder to acquire and retain.
Compromised performance
SecDevOps can also easily distract teams from improving performance, as shifting their entire focus to eliminating risk may distract from a business's primary goal. Thus, the right balance between security and speed is a priority. Remember, security means managed risk, not the elimination of risk.
Cultural and organizational resistance
Teams accustomed to traditional development practices often resist the shift to SecDevOps. The organizational culture might prioritize speed over security, leading to reluctance to adopt new processes. To overcome this, clear communication, training, and demonstrating the long-term benefits of SecDevOps—such as improved security and reduced risks—can help build acceptance.
Balancing speed with security
Maintaining development speed while implementing strong security measures is a key challenge in SecDevOps. Teams may feel pressured to prioritize faster releases, potentially compromising security. The solution lies in automating security processes and integrating them early, ensuring speed and security work hand-in-hand without causing delays.
Tool integration
Integrating security tools into existing DevOps toolchains can be complex and might disrupt established workflows. Ensuring smooth integration without overwhelming developers requires selecting tools that complement the current environment. Careful planning and testing are essential to prevent slowdowns or conflicts in the development process.
Visibility and monitoring
Monitoring security vulnerabilities and maintaining pipeline visibility is a significant challenge in SecDevOps. Real-time reporting helps to detect and address security issues promptly. Implementing comprehensive monitoring solutions also helps ensure teams can identify threats early and take prompt action.
Nine best practices for a successful SecDevOps workflow
Moving security to the left is a long-term process that requires accepting security as everyone's responsibility. A great starting point for organizations facing security vulnerabilities in their DevOps development workflow is to refer to The Rugged Manifesto, created by Josh Corman, David Rice, and Jeff Williams in 2010.
Once this new mindset is established, you should adopt the following practices to achieve a successful SecDevOps workflow.
1. Automate security measures
Security experts are expensive and difficult to hire. According to JFrog documentation, the current developer-to-security team ratio is 200:1. While achieving a more balanced ratio is a long-term goal, in the short term, automation can help your organization accomplish more with the same number of people.
The OWASP DevSecOps Automation Matrix (DAM) offers 64 key controls for security engineers, DevOps teams, and CISOs to leverage automation and build security directly into their development process.
Leveraging automation for security processes is crucial in a SecDevOps environment. Automating security measures saves time and ensures consistent and reliable security practices are applied throughout the development lifecycle.
Start by integrating automated security testing tools into your CI/CD pipelines. Tools like OWASP ZAP, Selenium, and Burp Suite can perform various security checks, from vulnerability scanning to penetration testing, without manual intervention. These tools can continuously monitor code for security flaws, providing instant feedback to developers.
2. Componentize applications
Smaller, isolated, manageable, and independently deployable components (i.e., microservices) allow security teams to test one area of an application at a time. This means you don't have to test the entire application at once. Each component can be configured independently, allowing for unique security tests to be integrated into your continuous integration/continuous deployment (CI/CD) pipeline.
Also, logging becomes more straightforward as each component generates its own logs, which can later be aggregated and analyzed with tools like the ELK stack or Splunk.
3. Shift left with security testing
You can ensure security is "baked in" early in your SDLC via a variety of security testing methods, including:
Static application security testing (SAST): Examines application source code, or binary code, for vulnerabilities; does not involve code execution
Dynamic application security testing (DAST): Reviews apps by executing the source code and simulating attacks
Interactive application security testing (IAST): A hybrid security testing approach that combines elements of SAST and DAST. IAST tools analyze an application from within, using instrumentation to provide real-time insights into vulnerabilities during execution.
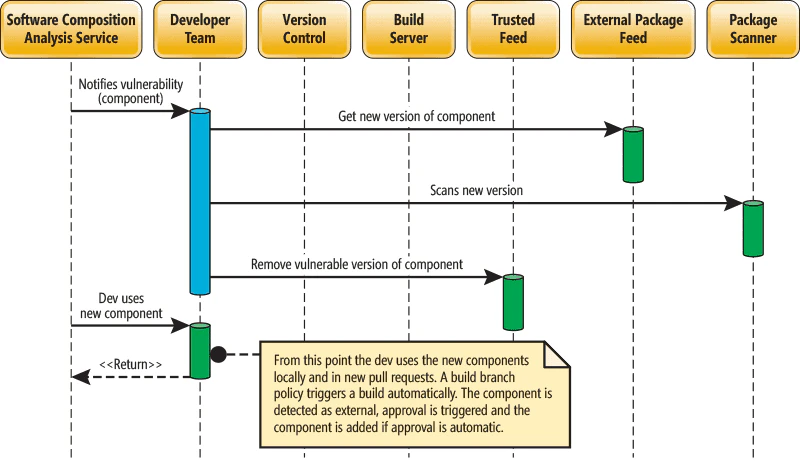
Software composition analysis (SCA): Test third-party and open-source app dependencies to identify Common Vulnerabilities and Exposures (CVEs)
IaC Security (Infrastructure as Code Security): Security practices applied to infrastructure provisioning scripts (e.g., Terraform, CloudFormation, Dockerfile, Helm and Kubernetes manifests, etc.). IaC security ensures that infrastructure configurations are secure and compliant with policies before deployment.
Secrets detection: The process of detecting and identifying sensitive information such as API keys, passwords, and tokens that are accidentally hardcoded into source code repositories. This helps prevent unauthorized access to systems and data.
Threat modeling: Detects potential security issues, with security and dev teams working on various possible scenarios.
4. Establish feedback loops between security teams and DevOps
Ongoing communication between security and DevOps teams is crucial for the rapid identification and resolution of security issues. This ensures that potential vulnerabilities do not progress unchecked through the development cycle.
Maintaining open communication allows teams to share insights, leading to timely interventions, effective threat mitigation, and stronger software integrity.
Continuous feedback loops help to create a culture of shared responsibility, where security is not seen as a standalone function but rather an integral part of the development process.
Regular engagement through meetings, code reviews, and automated alert systems ensures that security considerations are consistently addressed, leading to shorter remediation times and more resilient software products.
5. Implement security as code (SaC)
SaC is a practice where developers create and document security policies and checks directly as code. These secure code practices act more like guardrails to help reduce the attack surface. Tools such as CodeQL and Semgrep SAST help automate this process.
By writing security policies as code, you ensure consistency and repeatability when applying them across various environments. This approach enables easier audits and reviews since security definitions are stored in a version-controlled system, making them traceable and transparent.
The automation involved with SaC eliminates the manual overhead, reducing human error and speeding up the detection of vulnerabilities. To implement SaC effectively, start by establishing clear security policies and guidelines. Next, integrate tools like CodeQL and Semgrep into your CI/CD pipeline to automate security scans.
6. Engage and train developers in security
Developers need a security-first mindset, which can be supported by proper training, leadership, and security certifications. Organizations should invest in developer-focused security training and regular workshops to keep their staff updated on the latest threats and best practices.
Providing access to security certifications can further help developers, bolstering their confidence and competence in implementing security measures. Practical training, such as hands-on labs and real-world attack simulations, can give developers tangible experience in identifying and mitigating vulnerabilities.
7. Enhanced monitoring and response capabilities
Monitoring enables organizations to promptly detect and address security issues for faster, improved incident response. Depending on your use case, various monitoring tools are available on the market; these include Prometheus, Grafana, ELK stack, Falco, Splunk, and Datadog.
In addition to using tools like Prometheus and Grafana for metrics and visualization, consider using SIEM solutions such as Splunk for log management and analysis. Employing automated incident response systems can further speed up the identification and remediation process.
8. Manage dependencies securely
In modern software development, having secure coding practices is not enough.
It's impossible not to rely on dependencies and write everything from scratch since these components bring much value to a product/service. Of course, depending on these external dependencies also makes your applications vulnerable. This issue may compound when you have further sub-dependencies, which may also be vulnerable. For example, even if a primary dependency is considered secure, it might use other libraries that are outdated or have known security flaws.
It is critical to ensure the security of your dependencies. This can include setting up a central repository and package scanning procedure for installed dependencies. Tools such as Wiz or GitHub's dependency review can be used for vulnerability scanning. Projects may also require regular code reviews to ensure the latest version.
9. Integrate compliance checks
In a SecDevOps setting, integrated compliance checks involve building security and compliance controls into the software development and deployment process early on. These can be archived using several techniques including:
Automated security scanning
Compliance monitoring in CI/CD pipelines
Infrastructure compliance.
Integrating compliance checks early in the development and deployment processes ensures that your software adheres to regulatory standards and organizational policies from day one. Start by incorporating policy as code to automate and enforce compliance rules within your infrastructure as code (IaC). Use automated security scanning tools that continuously monitor your CI/CD pipelines, flagging compliance violations as part of routine code checks.
Mitigate security risks in the cloud with Wiz
As organizations strive to balance speed, performance, and security, SecDevOps offers a framework where security becomes a shared responsibility, ingrained in the culture and processes of developer, security, and operations teams.
Going forward, SecDevOps practices will likely focus on:
Enhancing integration tools and methodologies
Improving the seamless automation of security checks
Fostering a deeper cultural shift towards security across all phases of development
Solutions like Wiz offer comprehensive security and compliance monitoring across SecDevOps workflows. Wiz's ability to shift security left by providing deep insights into the health of your DevOps lifecycle ensures your infrastructure will remain secure and compliant.
Here's how Wiz can help optimize your organization’s SecDevOps workflows:
Continuous security monitoring: Wiz continuously monitors your cloud infrastructure for potential vulnerabilities and misconfigurations. This real-time security overview ensures immediate identification and remediation of issues before they become critical, aligning smoothly with SecDevOps practices.
Shift-left security insights: By integrating security checks early in the development lifecycle, Wiz provides actionable insights that enable your teams to detect and fix vulnerabilities in the initial stages of development. This proactive approach minimizes the risk of security breaches later in the process.
Automated compliance checks: Wiz automates compliance audits and ensures that your infrastructure adheres to regulatory standards such as GDPR, HIPAA, and PCI-DSS. This automation reduces manual effort, enabling your team to focus on delivering high-quality, secure applications faster.
Advanced threat detection: Using advanced machine learning and data analytics, Wiz effectively detects sophisticated threats across your cloud environments. This capability ensures your applications are safeguarded against evolving security dangers.
See for yourself how our industry-leading platform can secure your SecDevOps processes and the rest of your cloud infrastructure. Schedule a demo today.
Secure your SDLC from start to finish
See why Wiz is one of the few cloud security platforms that security and devops teams both love to use.