Wiz ranked as the #1 CSPM, CNAPP & CDR by G2
Protect Everything
You Build and Run in the Cloud
Wiz delivers context-driven insights needed to remove the most critical cloud risks and protect your sensitive assets.
|
747 reviews
Trusted by more than 50% of Fortune 100 companies
The reviews are in
Customers rate Wiz
#1 in cloud security
747 Reviews
Unified Cloud Security Platform
Wiz connects in minutes via API and achieves full coverage across PaaS resources, virtual machines, containers, serverless functions or sensitive data stored in public buckets, data volumes and databases without disrupting your business operations or requiring ongoing maintenance. It scales to any cloud environment with zero impact on resource or workload performance.
The Wiz Security Graph analyzes the relationships between technologies running in your cloud environment and immediately uncovers the most critical pathways to a breach. Query complex relationships across cloud layers enriched with meaningful context, all from a single console. Humanize risk with simple and intuitive graph visualization that anyone can understand without cloud or security expertise.
A single list of prioritized issues of toxic combinations of risk that have a high probability of being exploited and would lead to significant business impact. Simply understand what is the best next action for your teams to take, enabling all your teams to collaborate and improve your security and compliance posture.
Out-of-the-box coverage for the threats targeting cloud. Know the most important emerging threats you need to pay attention to right now. Immediately identify and remidiate the resources that are impacted and report confidently on impact.
Projects group your cloud environments based on ownership, so each team can own their own risks. A powerful role-based access control (RBAC) system models your organization structure into Wiz by grouping cloud resources according to their users or business purpose via a custom access framework.
Automatically correlate running cloud resources back to the code, pipeline, and developer that created and built it. Generate a 1-click fix in code with a pull request in your version control system to streamline remediation. Give developers cloud and security context in their IDE to give immediate feedback to code securely from the start.
Complete cloud context and automated forensics collection allows incident responders to identify the root cause of any incident. The correlation from detection, to resource, all the way back to code enables hardening at the source, removing classes of risk from being deployed.
Runtime protection from the Wiz Sensor stops threats and provides deep, real-time threat detection with context for better prioritization. When combined with comprehensive agentless coverage, it delivers a security solution specifically designed for cloud environments.
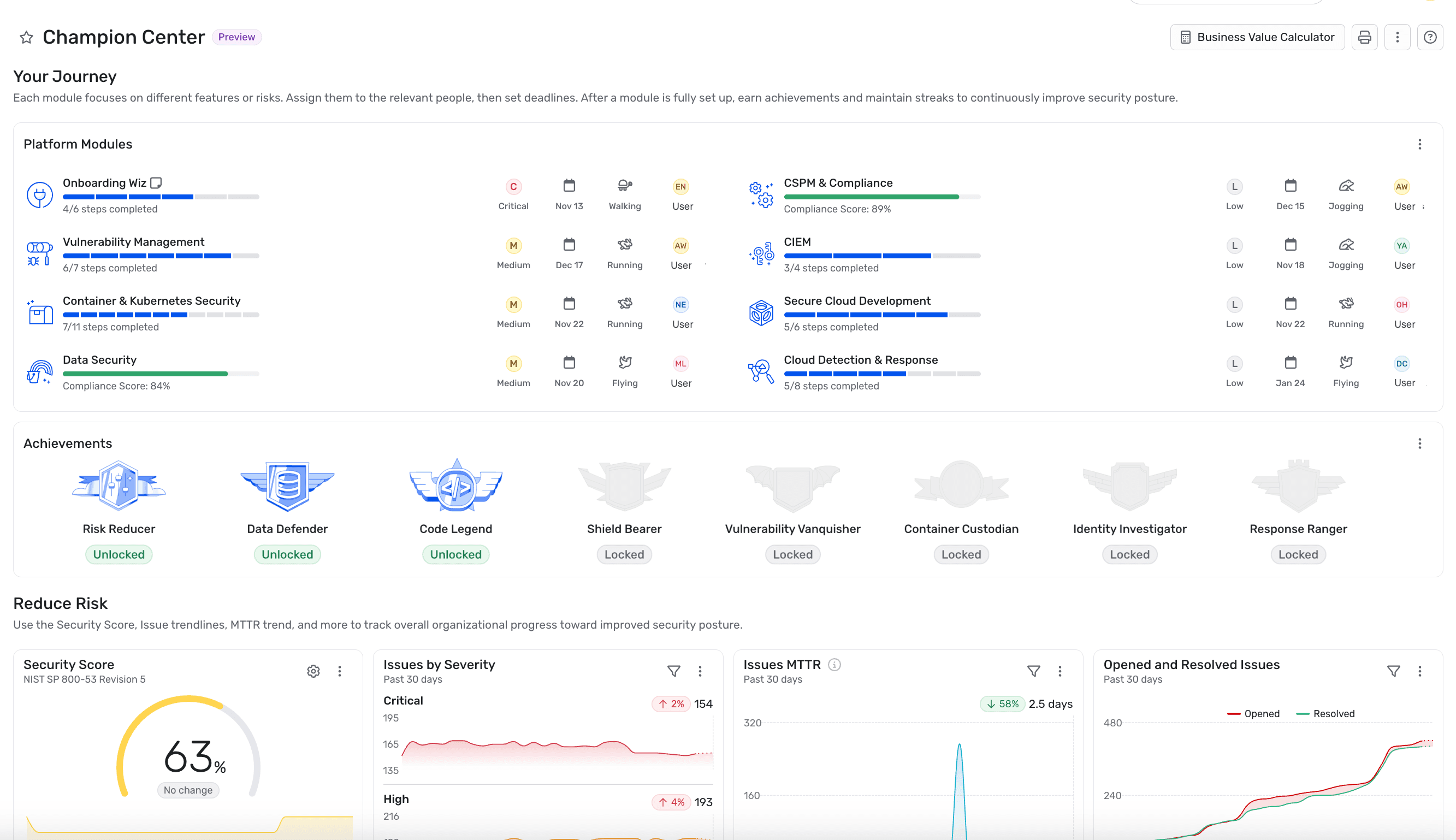
Gain centralized insights into Wiz adoption, security posture, and key achievements. The Champion Center gives leaders a complete picture of their cloud security program’s maturity.
Interactive product tour
Experience the
Wiz platform today

Secure your cloud
Effectively eliminate your most critical cloud risks with a unified platform that protects your sensitive assets
Unconditional visibility
Connect within minutes using API connectors to scan and take inventory of your entire cloud environment. Understand the interconnections between technologies running in your cloud and immediately visualize the pathways to a breach with the Wiz Security Graph.
Critical risk reduction
Identify toxic combinations of risks across misconfigurations, vulnerabilities, public exposure, excessive permissions, sensitive data and more to eliminate the attack paths that truly matter.
Democratize to developers
Enable teams to self-service the risks they own with high-fidelity alerting that reduces noise, automated remediation workflows in the tools they already use, and role-based segmentation of the cloud environment.
A Unified Platform
One Cloud Operating Model
to Run Faster, Safely
Break siloes between your engineering and security teams for continuous security improvement
Explore the platformSecure Cloud Development
Unified visibility and security across code, CI/CD, and cloud environments
Manage Security Posture
Agentless visibility & risk prioritization that proactively reduces the attack surface
Respond to Cloud Threats
Runtime protection & threat detection and response born for cloud
Get a personalized demo
Ready to see Wiz in action?
"Best User Experience I have ever seen, provides full visibility to cloud workloads."
"Wiz provides a single pane of glass to see what is going on in our cloud environments."
"We know that if Wiz identifies something as critical, it actually is."